There is a broad consensus today on the need to strengthen the individuals’ control on the management of their personal data. But the way to achieve this goal is still debatable.
Centralized solutions, including the majority of personal data lockers/vaults, are putting all their efforts on securing the servers. However, as recently demonstrated by the PRISM affair, no server is inviolable. The massive accumulation of personal data of millions of people in a single point only stirs up the coveting by minimizing the cost/benefit ratio of an attack.
Today, personal data are still organized in silos, each remaining under the control of the organization able to capture that piece of information (e.g., mobility traces, power consumption, telephone calls, web searches, medical data, etc.). The interest of crossing data from multiple silos is strong, from both the economic and societal point of views, and leads some organizations to gain the control over multiple silos, thereby increasing the threats to individual privacy.
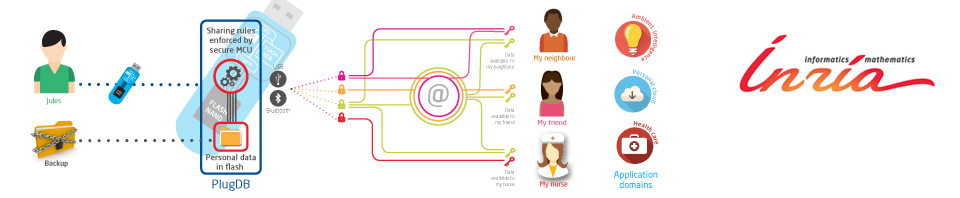
Oppositely, the Personal Server approach bets on decentralization. Each individual hosts his own data and controls the way the data is stored, exchanged, and crossed. By nature, the decentralization maximizes the cost/benefit ratio of an attack, since the server of each individual has to be attacked separately.
Nevertheless, the Personal Server approach raises two problems: (1) how can the average person – not a computer specialist – ensure the security of a personal data hosting device against malicious access, viruses, Trojans and face failures resulting in data loss and (2) how to maintain the economic or societal benefits offered by the global data processing on a population of individuals (e.g., behavioral or epidemiological study)?
PlugDB addresses these two problems by a combination of hardware solutions (smart card hardware security) and software solutions (embedded data management and access control, durability and data recovery in the event of data loss, distributed global treatments preserving the anonymity).
Next: How does it work ?