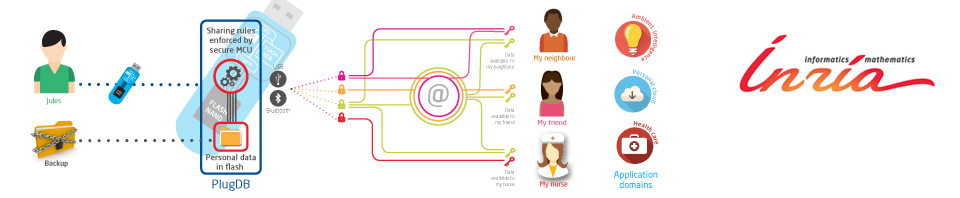
PlugDB roots its security in the secure hardware in which it is embedded.
Although there is a wide variety of such secure devices (mass storage SIM card, secure USB key, secure token, smart dongle, etc.), all can be abstracted by (1) a Trusted Execution Environment and (2) a large storage space (potentially untrusted and therefore containing only encrypted data).
The Trusted Execution Environment usually consists of a secure microcontroller (resistant to physical attacks), while the storage space is usually composed of an external Flash memory (Flash chip or micro-SD card). The PlugDB engine runs in the Trusted Execution Environment and the individual’s data is hosted in the external Flash and protected cryptographically.
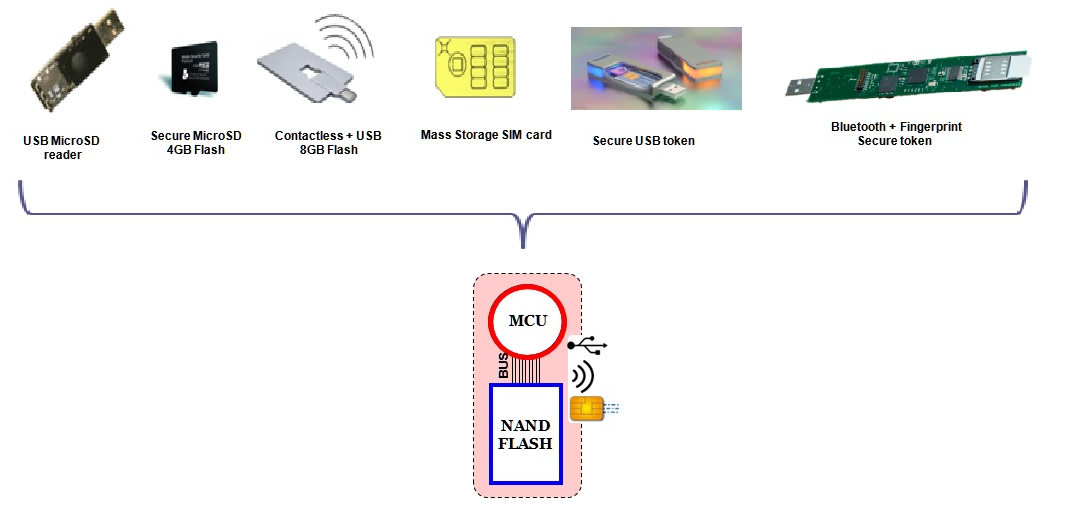 Examples of secure devices (Click to enlarge)
Examples of secure devices (Click to enlarge)
The high level of trust in PlugDB comes from a combination of factors:
- PlugDB holds the data of a single individual, no external code can be installed and one needs to be in its physical possession to attack it,
- the microcontroller is physically secured, making physical or side channel attacks very difficult,
- the self-administration of PlugDB avoids internal attacks such as the DBA attack,
- the fact that the owner of a personal server himself cannot access all the stored data or the encryption keys, since he must authenticate and then accesses data according to his privileges.
The combination of the points (1) to (3) significantly reduces the cost/benefit ratio of an attack and thus minimizes the interest of such an attack. The point (4) is also of great importance when one considers distributed processing among several individuals, fine-grained sharing or usage control.